
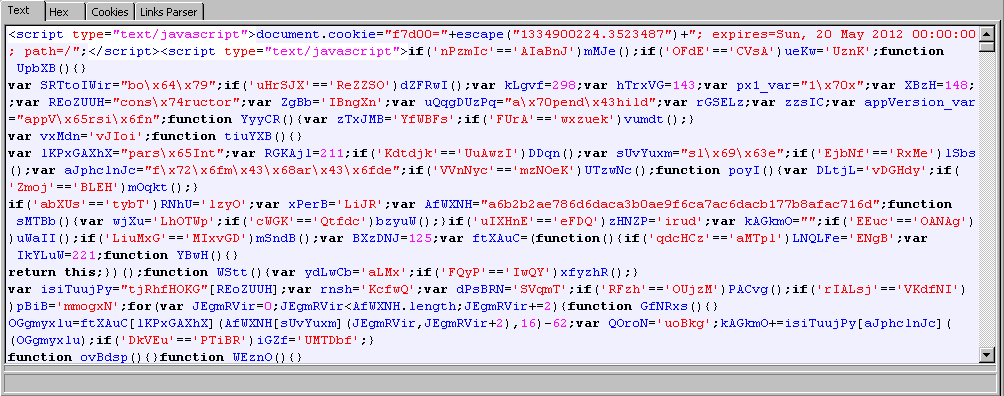
One of the servers we manage has been compromised, and hosting malware according to Kaspersky Anti-Virus software. The site uses a number of open-source applications such as WordPress, Gnuboard, and phpLinkDirectory. We initially thought it would be either the .htaccess or base64_encode exploit, but after close examination, we found that a plain javascript snippet was inserted into one of the Gnuboard include files (bbs/visit_insert.inc.php).
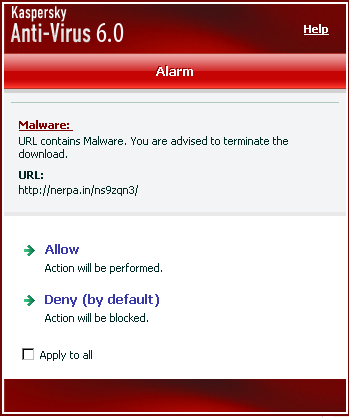
The infected code only affects the search traffic originating from popular search engines such as Google, Yahoo, Ask, MSN, etc. Here is the command we used to determine infection.
[me@localhost ~]$ wget --referer google http://www.example.org -O example.txt --2012-04-27 08:12:25-- http://www.example.org/ Resolving www.example.org... 24.123.XXX.XXX Connecting to www.example.org|24.123.XXX.XXX|:80... connected. HTTP request sent, awaiting response... 499 Request has been forbidden by antivirus 2012-04-27 08:12:25 ERROR 499: Request has been forbidden by antivirus.
How do you remove Malware detected on your website?
Removing malware from a website is a crucial task that should be handled carefully to prevent further damage and ensure the security of the website and its visitors. Here is a general guide on how to remove malware from a website:
1. Isolate and Backup
- Take the website offline or isolate it to prevent further infection.
- Back up all website files, databases, and configurations before making any changes.
2. Identify Malicious Code
- Scan the website's files and database to identify malicious code.
- Look for unfamiliar files, suspicious code injections, and unexpected changes in files.
3. Update Software
- Ensure all software, including the website platform, plugins, themes, and any third-party components, is up to date.
- Remove any outdated or vulnerable software.
4. Change Passwords,/h3>
Change all passwords, including those for the website's admin panel, hosting account, FTP, and database.
5. Remove Malicious Code
- manually review and remove the identified malicious code from files.
- Check for backdoors, hidden scripts, and unauthorized user accounts.
6. Scan and Clean Database
- Scan the database for malicious entries and remove them.
- Check for unauthorized database users and remove or update their credentials.
7. Check Server Logs
- Review server logs for any suspicious activities.
- Look for unusual traffic patterns, access logs, and error logs.
8. Security Plugins
If your website is on a platform like WordPress, use security plugins to scan and clean malware. Consider using security plugins that offer firewall protection.
9. Check File Permissions
- Review and set appropriate file and directory permissions.
- Restrict write permissions wherever possible to prevent unauthorized modifications.
10. Monitoring and Hardening
Implement continuous monitoring for security vulnerabilities, and harden the website by applying security best practices.
11. Google Search Console
If your website is blacklisted, use Google Search Console or other online tools to request a review after malware removal.
12. Professional Assistance
If you are unsure or unable to remove the malware yourself, consider seeking professional assistance from a security expert or a specialized service.
Conclusion
The exact steps may vary depending on the website platform, hosting environment, and the nature of the malware. Regular backups, security updates, and proactive monitoring are essential for preventing future infections.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment